做网站要主机还是服务器怎么做一个网站 免费
Ansible —— playbook 剧本
- 一、playbook的概述
- 1.playbook简介
- 2.什么是Ansible playbook剧本?
- 3.Ansible playbook剧本的特点
- 4.如何使用Ansible playbook剧本?
- 5.playbooks 本身由以下各部分组成
- 二、playbook示例
- 1.运行playbook
- 2.定义、引用变量
- 3.指定远程主机sudo切换用户
- 4.when条件判断
- 5.迭代
- 三、playbook模块
- 1.Templates 模块
- 2.tags 模块
- 3.Roles 模块
- 4.httpd模块
- 5.mysql模块
- 6.php模块
- 7.roles模块
一、playbook的概述
1.playbook简介
Ansible是一种强大的IT自动化工具,它的playbook剧本是其核心组件之一。playbook剧本使用YAML格式定义和描述一系列任务,将复杂的自动化配置和任务管理变得简单、易读和易于维护。本博客将介绍Ansible playbook剧本的基本概念、特点以及如何使用它来实现自动化配置和任务管理。
2.什么是Ansible playbook剧本?
playbook剧本是Ansible的核心组件之一,它是一个基于YAML格式的文件,用于定义和描述一系列任务。每个任务都对应一个具体的操作或配置。通过将多个任务组织成一个逻辑的流程,playbook剧本提供了一种结构化的方式来描述和管理复杂的自动化任务。
3.Ansible playbook剧本的特点
简洁易读:playbook剧本采用YAML语法,使得其语法简洁、易读、易写,提高了可维护性和可理解性。
灵活可扩展:playbook剧本支持变量、循环、条件判断等功能,可以实现复杂的逻辑和动态配置,并具备模块化的设计,通过引用不同的模块来实现不同的功能需求。
并行执行和多台主机管理:Ansible的playbook剧本支持并行执行和多台主机的管理,适用于处理大规模和分布式的场景。
4.如何使用Ansible playbook剧本?
- 全面了解Ansible机制和功能:在使用playbook剧本之前,需要对Ansible的基本概念和运作方式有一个全面的了解。
- 规划和组织playbook剧本的结构:一个良好的playbook剧本应该清晰地划分任务、模块和变量的作用域,并具备良好的注释和文档。
- 利用丰富的模块库和插件生态系统:合理利用Ansible的丰富模块库和插件,以提高playbook剧本的复用性和扩展性。
5.playbooks 本身由以下各部分组成
- Tasks:任务,即通过 task 调用 ansible 的模板将多个操作组织在一个 playbook 中运行
- Variables:变量
- Templates:模板
- Handlers:处理器,当changed状态条件满足时,(notify)触发执行的操作
- Roles:角色
二、playbook示例
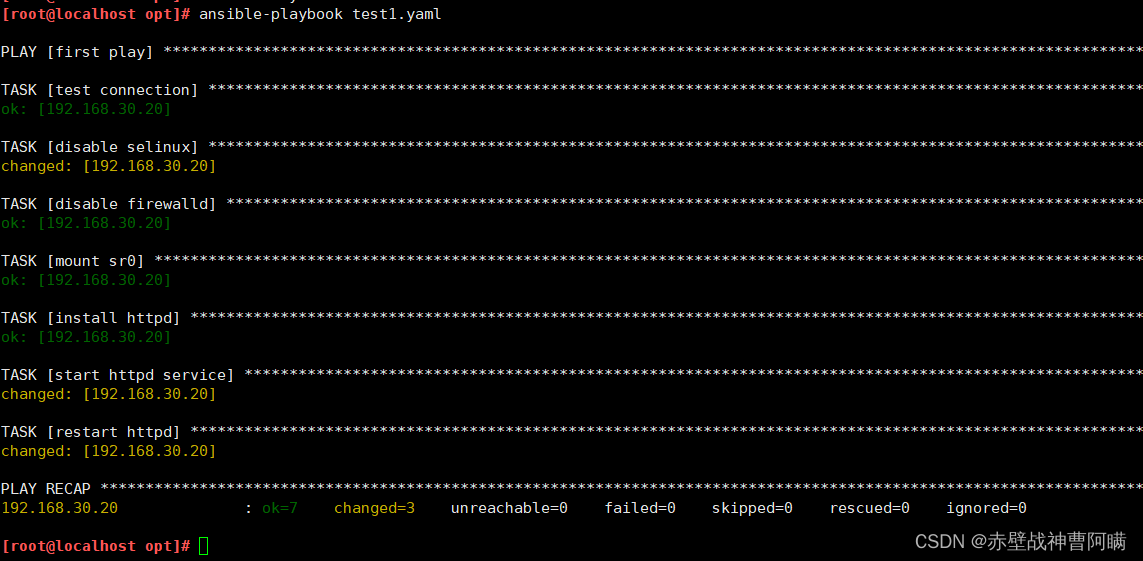
vim test1.yaml
--- #yaml文件以---开头,以表明这是一个yaml文件,可省略
- name: first play #定义一个play的名称,可省略gather_facts: false #设置不进行facts信息收集,这可以加快执行速度,可省略hosts: webservers #指定要执行任务的被管理主机组,如多个主机组用冒号分隔remote_user: root #指定被管理主机上执行任务的用户tasks: #定义任务列表,任务列表中的各任务按次序逐个在hosts中指定的主机上执行- name: test connection #自定义任务名称ping: #使用 module: [options] 格式来定义一个任务- name: disable selinuxcommand: '/sbin/setenforce 0' #command模块和shell模块无需使用key=value格式ignore_errors: True #如执行命令的返回值不为0,就会报错,tasks停止,可使用ignore_errors忽略失败的任务- name: disable firewalldservice: name=firewalld state=stopped #使用 module: options 格式来定义任务,option使用key=value格式- name: install httpdyum: name=httpd state=latest- name: install configuration file for httpdcopy: src=/opt/httpd.conf dest=/etc/httpd/conf/httpd.conf #这里需要一个事先准备好的/opt/httpd.conf文件notify: "restart httpd" #如以上操作后为changed的状态时,会通过notify指定的名称触发对应名称的handlers操作- name: start httpd serviceservice: enabled=true name=httpd state=startedhandlers: #handlers中定义的就是任务,此处handlers中的任务使用的是service模块- name: restart httpd #notify和handlers中任务的名称必须一致service: name=httpd state=restarted
##Ansible在执行完某个任务之后并不会立即去执行对应的handler,而是在当前play中所有普通任务都执行完后再去执行handler,这样的好处是可以多次触发notify,但最后只执行一次对应的handler,从而避免多次重启。
1.运行playbook
ansible-playbook test1.yaml
//补充参数:
-k(–ask-pass):用来交互输入ssh密码
-K(-ask-become-pass):用来交互输入sudo密码
-u:指定用户
ansible-playbook test1.yaml --syntax-check #检查yaml文件的语法是否正确
ansible-playbook test1.yaml --list-task #检查tasks任务
ansible-playbook test1.yaml --list-hosts #检查生效的主机
ansible-playbook test1.yaml --start-at-task='install httpd' #指定从某个task开始运行
2.定义、引用变量
- name: second playhosts: dbserversremote_user: rootvars: #定义变量- groupname: mysql #格式为 key: value- username: nginxtasks:- name: create groupgroup: name={{groupname}} system=yes gid=306 #使用 {{key}} 引用变量的值- name: create useruser: name={{username}} uid=306 group={{groupname}} - name: copy filecopy: content="{{ansible_default_ipv4}}" dest=/opt/vars.txt #在setup模块中可以获取facts变量信息ansible-playbook test1.yaml -e "username=nginx" #在命令行里定义变量
3.指定远程主机sudo切换用户
---
- hosts: dbserversremote_user: zhangsan become: yes #2.6版本以后的参数,之前是sudo,意思为切换用户运行become_user: root #指定sudo用户为root
执行playbook时:ansible-playbook test1.yml -k -K
4.when条件判断
在Ansible中,提供的唯一一个通用的条件判断是when指令,当when指令的值为true时,则该任务执行,否则不执行该任务。
`when一个比较常见的应用场景是实现跳过某个主机不执行任务或者只有满足条件的主机执行任务`
vim test2.yam
---
- hosts: allremote_user: roottasks:- name: shutdown host command: /sbin/shutdown -r nowwhen: ansible_default_ipv4.address == "192.168.30.30" #when指令中的变量名不需要手动加上 {{}}
或 when: inventory_hostname == "<主机名>"ansible-playbook test2.yaml
5.迭代
Ansible提供了很多种循环结构,一般都命名为with_items,作用等同于 loop 循环。
vim test3.yaml
---
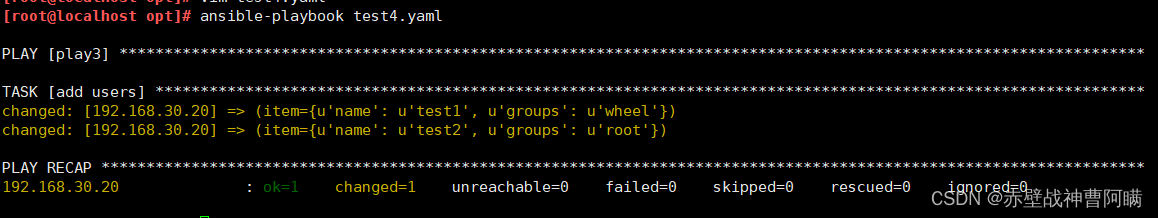
- name: play1hosts: dbserversgather_facts: falsetasks: - name: create filefile:path: "{{item}}"state: touchwith_items: [ /opt/a, /opt/b, /opt/c, /opt/d ]- name: play2hosts: dbserversgather_facts: false vars:test:- /tmp/test1- /tmp/test2- /tmp/test3- /tmp/test4tasks: - name: create directoriesfile:path: "{{item}}"state: directorywith_items: "{{test}}"- name: play3hosts: dbserversgather_facts: falsetasks:- name: add usersuser: name={{item.name}} state=present groups={{item.groups}}with_items:- name: test1groups: wheel- name: test2groups: root
或with_items:- {name: 'test1', groups: 'wheel'}- {name: 'test2', groups: 'root'}ansible-playbook test3.yaml
三、playbook模块
1.Templates 模块
Jinja是基于Python的模板引擎。Template类是Jinja的一个重要组件,可以看作是一个编译过的模板文件,用来产生目标文本,传递Python的变量给模板去替换模板中的标记。
1.先准备一个以 .j2 为后缀的 template 模板文件,设置引用的变量
cp /etc/httpd/conf/httpd.conf /opt/httpd.conf.j2vim /opt/httpd.conf.j2
Listen {{http_port}} #42行,修改
ServerName {{server_name}} #95行,修改
DocumentRoot "{{root_dir}}" #119行,修改2.修改主机清单文件,使用主机变量定义一个变量名相同,而值不同的变量
vim /etc/ansible/hosts
[webservers]
192.168.30.20 http_port=192.168.30.20:80 server_name=www.test1.com:80 root_dir=/etc/httpd/htdocs[dbservers]
192.168.30.30 http_port=192.168.30.30:80 server_name=www.test2.com:80 root_dir=/etc/httpd/htdocs3.编写 playbook
vim apache.yaml
---
- hosts: allremote_user: rootvars:- package: httpd- service: httpdtasks:- name: install httpd packageyum: name={{package}} state=latest- name: install configure filetemplate: src=/opt/httpd.conf.j2 dest=/etc/httpd/conf/httpd.conf #使用template模板notify:- restart httpd- name: create root dirfile: path=/etc/httpd/htdocs state=directory- name: start httpd serverservice: name={{service}} enabled=true state=startedhandlers:- name: restart httpdservice: name={{service}} state=restartedansible-playbook apache.yaml

2.tags 模块
可以在一个playbook中为某个或某些任务定义“标签”,在执行此playbook时通过ansible-playbook命令使用–tags选项能实现仅运行指定的tasks。
playbook还提供了一个特殊的tags为always。作用就是当使用always作为tags的task时,无论执行哪一个tags时,定义有always的tags都会执行。
vim webhosts.yaml
---
- hosts: webserversremote_user: roottasks:- name: Copy hosts filecopy: src=/etc/hosts dest=/opt/hoststags:- only #可自定义- name: touch filefile: path=/opt/testhost state=touchtags:- always #表示始终要运行的代码ansible-playbook webhosts.yaml --tags="only"vim dbhosts.yaml
---
- hosts: dbserversremote_user: roottasks:- name: Copy hosts filecopy: src=/etc/hosts dest=/opt/hoststags:- only- name: touch filefile: path=/opt/testhost state=touchansible-playbook dbhosts.yaml --tags="only"
//分别去两台被管理主机上去查看文件创建情况
3.Roles 模块
roles用于层次性、结构化地组织playbook。roles能够根据层次型结构自动装载变量文件、tasks以及handlers等。要使用roles只需要在playbook中使用include指令引入即可。
简单来讲,roles就是通过分别将变量、文件、任务、模板及处理器放置于单独的目录中,并可以便捷的include它们的一种机制。roles一般用于基于主机构建服务的场景中,但也可以是用于构建守护进程等场景中。主要使用场景代码复用度较高的情况下。
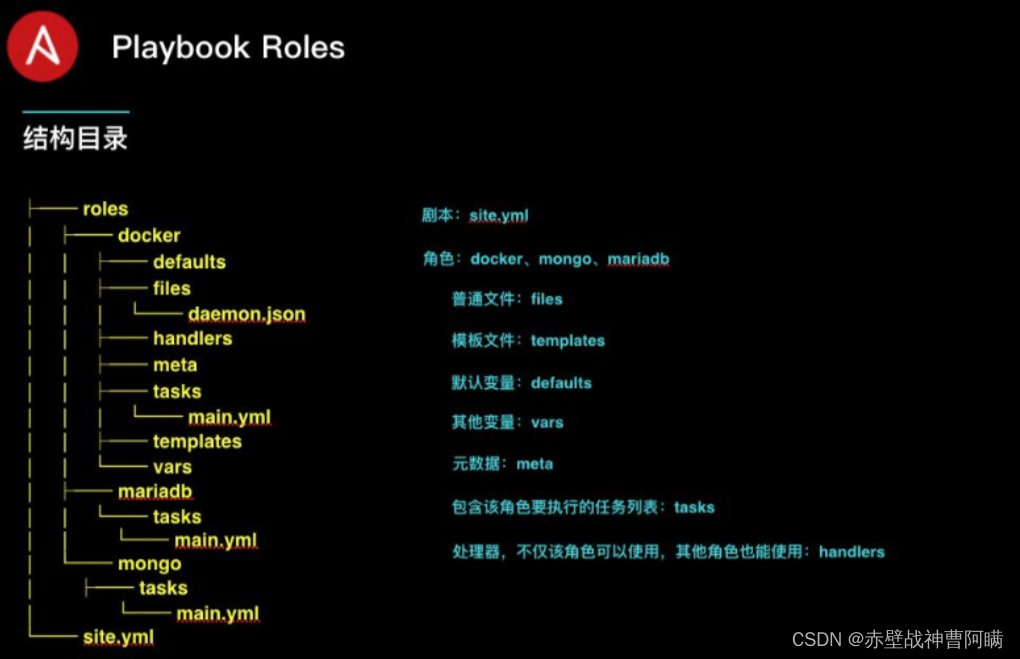
`roles 内各目录含义解释`
●files
用来存放由 copy 模块或 script 模块调用的文件。●templates
用来存放 jinjia2 模板,template 模块会自动在此目录中寻找 jinjia2 模板文件。●tasks
此目录应当包含一个 main.yml 文件,用于定义此角色的任务列表,此文件可以使用 include 包含其它的位于此目录的 task 文件。●handlers
此目录应当包含一个 main.yml 文件,用于定义此角色中触发条件时执行的动作。●vars
此目录应当包含一个 main.yml 文件,用于定义此角色用到的变量。●defaults
此目录应当包含一个 main.yml 文件,用于为当前角色设定默认变量。 这些变量具有所有可用变量中最低的优先级,并且可以很容易地被任何其他变量覆盖。所以生产中我们一般不在这里定义变量●meta
此目录应当包含一个 main.yml 文件,用于定义此角色的元数据信息及其依赖关系。
在一个 playbook 中使用 roles 的步骤:
`1.创建以 roles 命名的目录`
mkdir /etc/ansible/roles/ -p #yum装完默认就有`2.创建全局变量目录(可选)`
mkdir /etc/ansible/group_vars/ -p
touch /etc/ansible/group_vars/all #文件名自己定义,引用的时候注意`3.在 roles 目录中分别创建以各角色名称命名的目录,如 httpd、mysql`
mkdir /etc/ansible/roles/httpd
mkdir /etc/ansible/roles/mysql`4.在每个角色命名的目录中分别创建files、handlers、tasks、templates、meta、defaults和vars目录,用不到的目录可以创建为空目录,也可以不创建`
mkdir /etc/ansible/roles/httpd/{files,templates,tasks,handlers,vars,defaults,meta}
mkdir /etc/ansible/roles/mysql/{files,templates,tasks,handlers,vars,defaults,meta}`5.在每个角色的 handlers、tasks、meta、defaults、vars 目录下创建 main.yml 文件,千万不能自定义文件名`
touch /etc/ansible/roles/httpd/{defaults,vars,tasks,meta,handlers}/main.yml
touch /etc/ansible/roles/mysql/{defaults,vars,tasks,meta,handlers}/main.yml`6.修改 site.yml 文件,针对不同主机去调用不同的角色`
vim /etc/ansible/site.yml
---
- hosts: webserversremote_user: rootroles:- httpd
- hosts: dbserversremote_user: rootroles:- mysql`7.运行 ansible-playbook`
cd /etc/ansible
ansible-playbook site.yml`示例:`
mkdir /etc/ansible/roles/httpd/{files,templates,tasks,handlers,vars,defaults,meta} -p
mkdir /etc/ansible/roles/mysql/{files,templates,tasks,handlers,vars,defaults,meta} -p
mkdir /etc/ansible/roles/php/{files,templates,tasks,handlers,vars,defaults,meta} -ptouch /etc/ansible/roles/httpd/{defaults,vars,tasks,meta,handlers}/main.yml
touch /etc/ansible/roles/mysql/{defaults,vars,tasks,meta,handlers}/main.yml
touch /etc/ansible/roles/php/{defaults,vars,tasks,meta,handlers}/main.yml
4.httpd模块
写一个简单的tasks/main.yml
vim /etc/ansible/roles/httpd/tasks/main.yml
- name: install apacheyum: name={{pkg}} state=latest
- name: start apacheservice: enabled=true name={{svc}} state=started//定义变量:可以定义在全局变量中,也可以定义在roles角色变量中,一般定义在角色变量中
vim /etc/ansible/roles/httpd/vars/main.yml
pkg: httpd
svc: httpd
5.mysql模块
vim /etc/ansible/roles/mysql/tasks/main.yml
- name: install mysqlyum: name={{pkg}} state=latest
- name: start mysqlservice: enabled=true name={{svc}} state=startedvim /etc/ansible/roles/mysql/vars/main.yml
pkg:- mariadb- mariadb-server
svc: mariadb
6.php模块
vim /etc/ansible/roles/php/tasks/main.yml
- name: install phpyum: name={{pkg}} state=latest
- name: start php-fpmservice: enabled=true name={{svc}} state=startedvim /etc/ansible/roles/php/vars/main.yml
pkg:- php- php-fpm
svc: php-fpm
7.roles模块
vim /etc/ansible/site.yml
---
- hosts: webserversremote_user: rootroles:- httpd- mysql- phpcd /etc/ansible
ansible-playbook site.yml
